
MalwareDisciple
RE & code
Radare2 Demo – 20 tips
Radare2 Demo – 20 tips
Here is a quick demo to get REs/Malware Analysts started with what I think is the most underrated disassembler out right now.
Get it here: https://rada.re/n/radare2.html
Let’s dig into some code.
1 – Start Radare2 and point it at the sample you are analyzing.
$ r2 GreedyBastard.bin
-- Experts agree, security holes suck, and we fixed some of them!
[0x0048608f]>
2 – Have Radare2 analyze the sample. The more ‘a’s, the deeper the analysis.
[0x0048608f]> aaaa
[x] Analyze all flags starting with sym. and entry0 (aa)
[x] Analyze function calls (aac)
[x] Analyze len bytes of instructions for references (aar)
[x] Check for objc references
[x] Check for vtables
[x] Type matching analysis for all functions (aaft)
[x] Propagate noreturn information
[x] Use -AA or aaaa to perform additional experimental analysis.
[x] Finding function preludes
[x] Enable constraint types analysis for variables
[0x0048608f]>
3 – Take a look at the PE’s sections.
[0x0048608f]> iS
[Sections]
nth paddr size vaddr vsize perm name
―――――――――――――――――――――――――――――――――――――――――――――――――――――
0 0x00000400 0xa4400 0x00401000 0xa5000 -r-x .text
1 0x000a4800 0x28400 0x004a6000 0x29000 -r-- .rdata
2 0x000ccc00 0x9200 0x004cf000 0xd000 -rw- .data
3 0x000d5e00 0x200 0x004dc000 0x1000 -rw- .tls
4 0x000d6000 0x200 0x004dd000 0x1000 -r-- .gfids
5 0x000d6200 0x200 0x004de000 0x1000 -r-- .rsrc
6 0x000d6400 0x6c00 0x004df000 0x7000 -r-- .reloc
4 – Check out the imports
[0x0048608f]> ii
[Imports]
nth vaddr bind type name
―――――――――――――――――――――――――――――
1 0x004a60a8 NONE FUNC KERNEL32.dll_GlobalLock
2 0x004a60ac NONE FUNC KERNEL32.dll_DeleteCriticalSection
3 0x004a60b0 NONE FUNC KERNEL32.dll_GlobalUnlock
4 0x004a60b4 NONE FUNC KERNEL32.dll_ReadFile
5 0x004a60b8 NONE FUNC KERNEL32.dll_LoadLibraryA
6 0x004a60bc NONE FUNC KERNEL32.dll_FindFirstFileA
7 0x004a60c0 NONE FUNC KERNEL32.dll_GetGeoInfoA
8 0x004a60c4 NONE FUNC KERNEL32.dll_TerminateProcess
9 0x004a60c8 NONE FUNC KERNEL32.dll_GetDriveTypeA
10 0x004a60cc NONE FUNC KERNEL32.dll_SetFileTime
11 0x004a60d0 NONE FUNC KERNEL32.dll_FindNextFileA
12 0x004a60d4 NONE FUNC KERNEL32.dll_LockFile
13 0x004a60d8 NONE FUNC KERNEL32.dll_CreatePipe
14 0x004a60dc NONE FUNC KERNEL32.dll_WaitForSingleObject
15 0x004a60e0 NONE FUNC KERNEL32.dll_K32GetModuleFileNameExA
16 0x004a60e4 NONE FUNC KERNEL32.dll_GetFileAttributesA
17 0x004a60e8 NONE FUNC KERNEL32.dll_MoveFileExA
5 – Do the same for exports (different sample)
[0x10001000]> iE
[Exports]
nth paddr vaddr bind type size name
――――――――――――――――――――――――――――――――――――――――――――――――
0 0x00006ebc 0x10007abc GLOBAL FUNC 0 cryptopp.dll_DeleteMusic
1 0x00007f5f 0x10008b5f GLOBAL FUNC 0 cryptopp.dll_DllRegisterServer
2 0x000096c8 0x1000a2c8 GLOBAL FUNC 0 cryptopp.dll_FindMusic
3 0x000049c9 0x100055c9 GLOBAL FUNC 0 cryptopp.dll_MoveMusic
4 0x00002a7d 0x1000367d GLOBAL FUNC 0 cryptopp.dll_SeekMusic
5 0x000037d0 0x100043d0 GLOBAL FUNC 0 cryptopp.dll_UploadMusic
6 – Analysts love da strings
[0x10001000]> iz
[Strings]
nth paddr vaddr len size section type string
―――――――――――――――――――――――――――――――――――――――――――――――――――――――――
0 0x0000ea00 0x10010000 10 22 .rdata utf16le 2147483648
1 0x0000ea19 0x10010019 5 7 .rdata utf8 ccƄ|| blocks=Basic Latin,Latin Extended-B
2 0x0000ea2d 0x1001002d 5 7 .rdata utf8 kkֱoo blocks=Basic Latin,Hebrew
3 0x0000ea36 0x10010036 5 7 .rdata utf8 őP00` blocks=Latin Extended-A,Basic Latin
4 0x0000ea44 0x10010044 4 5 .rdata ascii }++V
5 0x0000eaa3 0x100100a3 13 14 .rdata ascii =j&&LZ66lA??~
6 0x0000eab6 0x100100b6 5 7 .rdata utf8 blocks=Combining Diacritical Marks,Basic Latin
7 0x0000eace 0x100100ce 6 8 .rdata utf8 ثS11b? blocks=Arabic,Basic Latin
8 0x0000eade 0x100100de 6 8 .rdata utf8 Ǖe##F^ blocks=Latin Extended-B,Basic Latin
9 0x0000eaf7 0x100100f7 4 5 .rdata ascii /\t\a\a
10 0x0000eb0c 0x1001010c 5 7 .rdata utf8 i''NͲ blocks=Basic Latin,Greek and Coptic
11 0x0000eb20 0x10010120 5 6 .rdata ascii t,,X.
7 – Find main (seek)
[0x0048608f]> s main
[0x004182c0]>
8 – Jump/seek to a virtual address
[0x004182c0]> s 0x0048608f
[0x0048608f]>
9 – Disassemble the function you are in
[0x004182c0]> pdf
; CALL XREF from entry0 @ 0x486018
;-- eip:
┌ 407: int main (int argc, char **argv, char **envp);
│ ; var int32_t var_2c0h @ ebp-0x2c0
│ ; var LPDWORD lpThreadId @ ebp-0x2bc
│ ; var int32_t var_2b8h @ ebp-0x2b8
│ ; var sockaddr *name @ ebp-0x128
│ ; var u_short var_126h @ ebp-0x126
│ ; var uint32_t var_124h @ ebp-0x124
│ ; var LPVOID lpParameter @ ebp-0x118
│ ; var int32_t var_14h @ ebp-0x14
│ ; var int32_t var_10h @ ebp-0x10
│ ; var int32_t var_ch @ ebp-0xc
│ ; var int32_t var_4h @ ebp-0x4
│ 0x004182c0 55 push ebp
│ 0x004182c1 8bec mov ebp, esp
│ 0x004182c3 6aff push 0xffffffffffffffff
│ 0x004182c5 6880504a00 push 0x4a5080
│ 0x004182ca 64a100000000 mov eax, dword fs:[0]
│ 0x004182d0 50 push eax
│ 0x004182d1 81ecb4020000 sub esp, 0x2b4
│ 0x004182d7 a124f34c00 mov eax, dword [0x4cf324] ; [0x4cf324:4]=0xbb40e64e ; "N\xe6@\xbb"
│ 0x004182dc 33c5 xor eax, ebp
│ 0x004182de 8945ec mov dword [var_14h], eax
│ 0x004182e1 53 push ebx
│ 0x004182e2 56 push esi
│ 0x004182e3 57 push edi
│ 0x004182e4 50 push eax
│ 0x004182e5 8d45f4 lea eax, [var_ch]
│ 0x004182e8 64a300000000 mov dword fs:[0], eax
│ 0x004182ee 8965f0 mov dword [var_10h], esp
│ 0x004182f1 e82aceffff call fcn.00415120
10 – Disassemble n lines of code
[0x004182d1]> pd 5
│ 0x004182d1 81ecb4020000 sub esp, 0x2b4
│ 0x004182d7 a124f34c00 mov eax, dword [0x4cf324] ; [0x4cf324:4]=0xbb40e64e ; "N\xe6@\xbb"
│ 0x004182dc 33c5 xor eax, ebp
│ 0x004182de 8945ec mov dword [var_14h], eax
│ 0x004182e1 53 push ebx
[0x004182d1]>
11 – Hex dump!
[0x004d7010]> x
- offset - 0 1 2 3 4 5 6 7 8 9 A B C D E F 0123456789ABCDEF
0x004d7010 0000 0000 3137 372e 3137 372e 3137 372e ....177.177.177.
0x004d7020 3137 3700 0000 0040 0300 0000 4800 0000 [email protected]...
0x004d7030 1004 0000 0000 0000 8867 4c00 0000 0000 .........gL.....
0x004d7040 b01a 4200 c01d 4200 c01e 4200 4020 4200 ..B...B...B.@ B.
0x004d7050 e021 4200 1022 4200 3022 4200 5022 4200 .!B.."B.0"B.P"B.
0x004d7060 6022 4200 1023 4200 9023 4200 1022 4200 `"B..#B..#B.."B.
0x004d7070 4023 4200 f0f8 4100 e0f9 4100 50fa 4100 @#B...A...A.P.A.
0x004d7080 70a7 4c00 0000 0200 78a7 4c00 0000 0400 p.L.....x.L.....
0x004d7090 0000 0000 0000 0000 88a7 4c00 0100 0000 ..........L.....
0x004d70a0 8ca7 4c00 0200 0000 90a7 4c00 0600 0000 ..L.......L.....
0x004d70b0 5490 4c00 8000 0000 0000 0000 0000 0000 T.L.............
0x004d70c0 0200 0108 0000 0000 0000 0000 20cb 4400 ............ .D.
0x004d70d0 0000 0000 0000 0000 7077 4c00 0000 0000 ........pwL.....
0x004d70e0 0000 0000 0200 0108 0000 0000 0000 0000 ................
0x004d70f0 10ce 4400 0000 0000 0000 0000 8477 4c00 ..D..........wL.
0x004d7100 0000 0000 0000 0000 0300 0108 0000 0000 ................
12 – Hexdump n bytes (decimal or hex)
[0x004d7010]> x 0x20
- offset - 0 1 2 3 4 5 6 7 8 9 A B C D E F 0123456789ABCDEF
0x004d7010 0000 0000 3137 372e 3137 372e 3137 372e ....177.177.177.
0x004d7020 3137 3700 0000 0040 0300 0000 4800 0000 [email protected]...
[0x004d7010]> x 32
- offset - 0 1 2 3 4 5 6 7 8 9 A B C D E F 0123456789ABCDEF
0x004d7010 0000 0000 3137 372e 3137 372e 3137 372e ....177.177.177.
0x004d7020 3137 3700 0000 0040 0300 0000 4800 0000 [email protected]...
[0x004d7010]>
13 – Cross reference! We can use this to find where the IP above is used in the binary.
[0x004182c0]> axt 0x004d7014
main 0x418392 [DATA] push str.177.177.177.177
14 – Seek to that address, and see what function this string is passed to.
[0x004182c0]> s 0x418392
[0x00418392]> pd 5
│ 0x00418392 6814704d00 push str.177.177.177.177
; 0x4d7014 ; "177.177.177.177"
│ 0x00418397 668985d8feff. mov word [name], ax
│ 0x0041839e ff15f4634a00 call dword
[sym.imp.WS2_32.dll_inet_addr] ; 0x4a63f4
│ 0x004183a4 6804704d00 push 0x4d7004 ; "80" ; int32_t arg_8h
│ 0x004183a9 8985dcfeffff mov dword [var_124h], eax
[0x00418392]>
15 – Radare2 also has a great graph view. Escape this view with ‘q’.
[0x00418392]> VV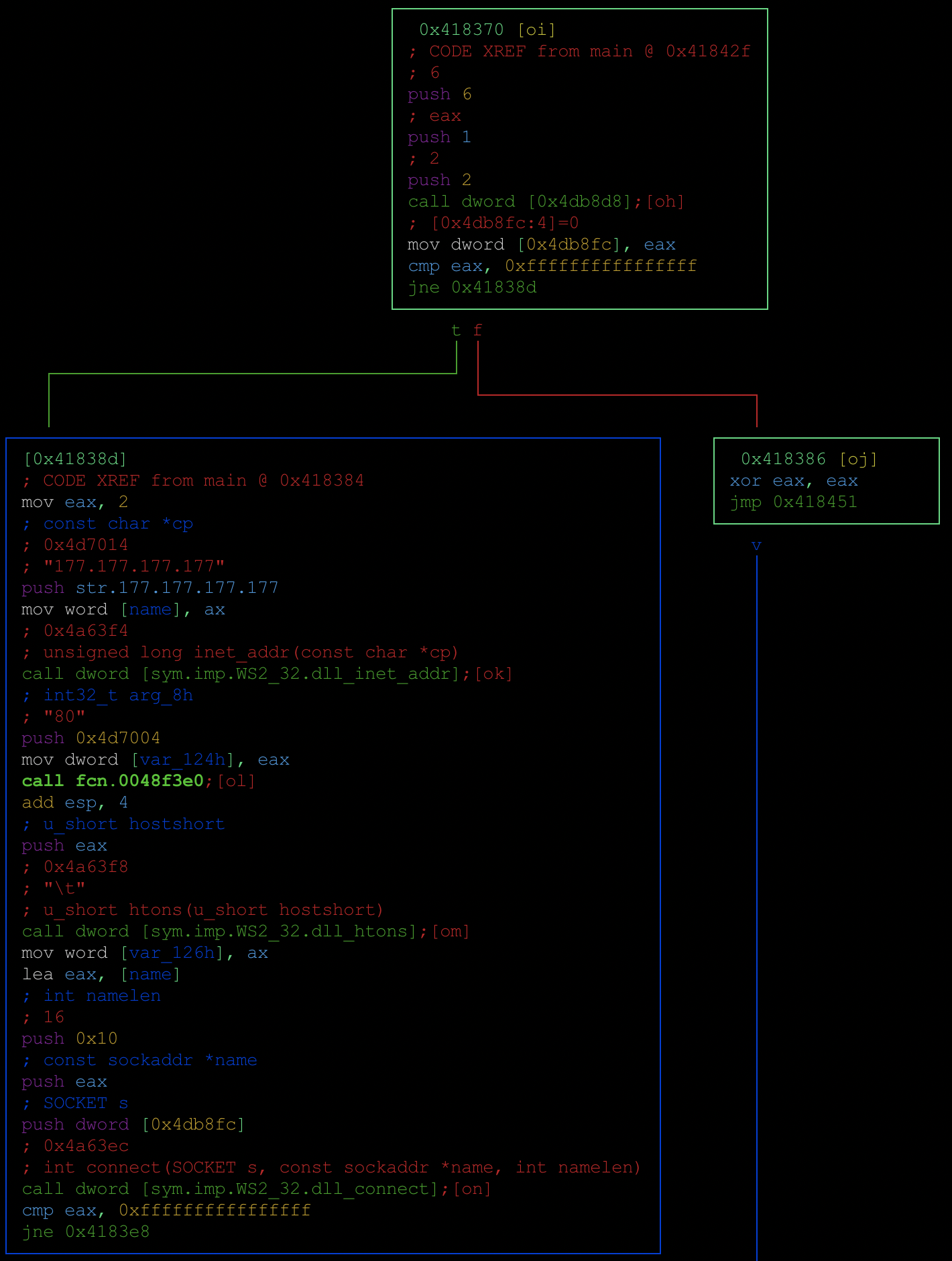
16 – Run bash commands
[0x004182c0]> ii | grep waveIn
1 0x004a63c8 NONE FUNC WINMM.dll_waveInStart
2 0x004a63cc NONE FUNC WINMM.dll_waveInClose
3 0x004a63d0 NONE FUNC WINMM.dll_waveInPrepareHeader
4 0x004a63d4 NONE FUNC WINMM.dll_waveInReset
5 0x004a63d8 NONE FUNC WINMM.dll_waveInUnprepareHeader
6 0x004a63dc NONE FUNC WINMM.dll_waveInOpen
7 0x004a63e0 NONE FUNC WINMM.dll_waveInAddBuffer
17 – Cross reference imports to see where they are used by the sample (using the above address for waveInStart). Then seek to that address and analyze the function.
[0x004182c0]> axt 0x004a63c8
fcn.00408750 0x408848 [CALL] call dword [sym.imp.WINMM.dll_waveInStart]
[0x004182c0]> s fcn.00408750
[0x00408750]> VV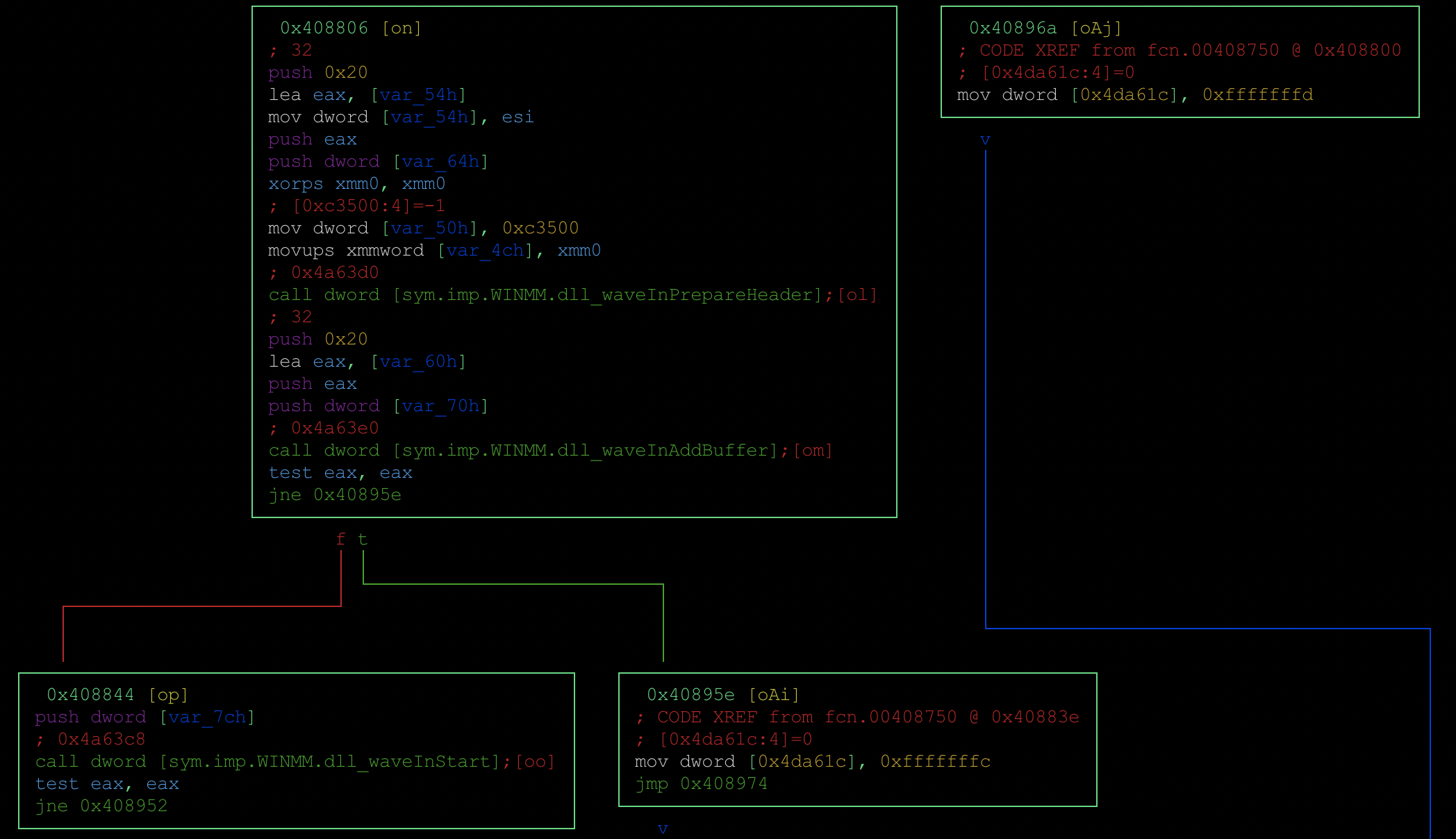
18 – Get a list of the sample’s functions
[0x10001000]> afl
0x10001000 7 66 entry0
0x10007abc 1 5 sym.cryptopp.dll_DeleteMusic
0x10008b5f 3 25 sym.cryptopp.dll_DllRegisterServer
0x1000e2a0 5 90 fcn.1000e2a0
0x10009f7c 24 311 fcn.10009f7c
0x1000a2c8 1 5 sym.cryptopp.dll_FindMusic
0x100055c9 1 5 sym.cryptopp.dll_MoveMusic
0x1000367d 1 5 sym.cryptopp.dll_SeekMusic
0x100043d0 1 5 sym.cryptopp.dll_UploadMusic
0x1000e4c0 3 77 fcn.1000e4c0
0x1000b2c7 1 6 sub.MSVCRT.dll_wcslen
0x1000e720 4 75 fcn.1000e720
0x1000e510 8 176 fcn.1000e510
0x1000eaf0 1 55 fcn.1000eaf0
0x1000b2cd 1 6 sub.KERNEL32.dll_TlsGetValue
0x1000eb30 1 53 fcn.1000eb30
0x1000b2e0 5 39 -> 36 fcn.1000b2e0
0x1000e5c0 5 70 -> 68 fcn.1000e5c0
0x1000e610 9 223 fcn.1000e610
0x1000e6f0 1 37 fcn.1000e6f0
0x1000b510 16 224 -> 217 fcn.1000b510
0x1000eb65 5 58 fcn.1000eb65
0x1000e770 1 44 fcn.1000e770
0x1000b5f0 11 137 fcn.1000b5f0
0x1000e7a0 1 48 fcn.1000e7a0
0x1000bb30 16 239 -> 236 fcn.1000bb30
0x1000b2b5 1 6 sub.MSVCRT.dll_wcsstr
0x1000b740 21 146 fcn.1000b740
0x1000b1f0 5 33 fcn.1000b1f0
0x1000b2bb 1 6 sub.MSVCRT.dll_memmove
0x1000b2c1 1 6 sub.MSVCRT.dll_memcpy
0x1000b0f4 1 6 sub.MSVCRT.dll_memset
0x1000e7d0 35 636 fcn.1000e7d0
0x1000dd91 5 46 fcn.1000dd91
19 – Find the entry point
[0x10001000]> ie
[Entrypoints]
vaddr=0x10001000 paddr=0x00000400 haddr=0x000000a8 type=program
1 entrypoints
20 – Seek backward/forward to where you have been in the binary. Just like the back button in IDA.
[0x0048608f]> s main
[0x004182c0]>
[0x004182c0]> s -
[0x0048608f]>
[0x0048608f]> s +
[0x004182c0]>This just scratches the surface of this super powerful tool. Here is the link to the official Radare2 book: https://radare.gitbooks.io/radare2book/content/
Enjoy!
Comments are closed.
2 replies on “Radare2 Demo – 20 tips”
I found Radare2 Explorations (https://monosource.gitbooks.io/radare2-explorations/content/) a useful practical guide to Radare2 as well.
For tip 16, if it’s just for grepping the output of Radare2’s commands, the ~ operator is more concise e.g. ii~waveIn (less typing required 🙂
Thanks for visiting, and thanks also for sharing!